Which Statement Best Describes This Public Service Campaign?
Enterprise Networking, Security, and Automation ( Version 7.00) – Modules 13 – 14: Emerging Network Technologies Exam
1. A visitor uses a cloud-based payroll system. Which cloud computing engineering is this company using?
- browser as a service (BaaS)
- infrastructure as a service (IaaS)
- software equally a service (SaaS)
- wireless every bit a service (WaaS)
2. For a information center, what is the difference in the server virtualization data traffic compared with the traditional client-server model?
- Data traffic from clients will be routed to multiple virtual servers.
- There are meaning information exchanges between virtual servers.
- At that place is more data traffic flowing from virtual servers to clients.
- More network control traffic is generated between virtual servers and clients.
3. Which component in a traditional infrastructure device provides Layer two and Layer 3 functions to create data paths within a network?
- data aeroplane
- command plane
- adjacency table
- forwarding information base
4. Which network traffic direction engineering science is a basic element in SDN implementations?
- OpenFlow
- OpenStack
- IEEE 802.1aq
- Interface to the Routing System
5. Which type of hypervisor would virtually likely be used in a data eye?
- Type two
- Blazon one
- Nexus
- Hadoop
6. Which is a feature of a Type 1 hypervisor?
- installed directly on a server
- best suited for consumers and not for an enterprise environment
- does not crave management panel software
- installed on an existing operating system
7. Which two layers of the OSI model are associated with SDN network control plane functions that make forwarding decisions? (Choose two.)
- Layer 1
- Layer 2
- Layer iii
- Layer 4
- Layer 5
8. What pre-populates the FIB on Cisco devices that utilise CEF to process packets?
- the routing table
- the adjacency table
- the ARP table
- the DSP
nine. What is a function of the information plane of a network device?
- sending data to the CPU for processing
- edifice the routing table
- resolving MAC addresses
- forwarding traffic flows
10. Which statement describes the concept of deject calculating?
- separation of application from hardware
- separation of management plane from control plane
- separation of operating organisation from hardware
- separation of control aeroplane from data aeroplane
11. Which deject model provides services for a specific organization or entity?
- a public deject
- a hybrid cloud
- a private cloud
- a community deject
12. What ii benefits are gained when an arrangement adopts cloud calculating and virtualization? (Choose two.)
- provides a "pay-as-y'all-go" model, assuasive organizations to care for computing and storage expenses as a utility
- enables rapid responses to increasing information volume requirements
- distributed processing of large information sets in the size of terabytes
- elimination of vulnerabilities to cyber attacks
- increases the dependance on onsite IT resources
thirteen. Which blazon of Hypervisor is implemented when a user with a laptop running the Mac OS installs a Windows virtual OS instance?
- blazon 2
- virtual auto
- type i
- blank metal
14. A small company is considering moving many of its data centre functions to the deject. What are iii advantages of this plan? (Choose three.)
- The visitor but needs to pay for the amount of processing and storage capacity that it uses.
- Cloud services are billed at a fixed fee no matter how much processing and storage are used past the company.
- The company does non demand to be concerned about how to handle increasing information storage and processing demands with in-firm data center equipment.
- The company tin can increase processing and storage capacity as needed and then subtract capacity when it is no longer needed.
- Unmarried-tenant data centers can easily abound to accommodate increasing data storage requirements.
- Cloud services enable the company to own and administer its ain servers and storage devices.
15. How does virtualization help with disaster recovery inside a information center?
- back up of live migration
- guarantee of power
- improvement of business practices
- supply of consistent air flow
16. What engineering science allows users to access data anywhere and at any time?
- Cloud computing
- virtualization
- micromarketing
- data analytics
17. Which action takes identify in the assurance element of the IBN model?
- verification and corrective action
- configuring systems
- translation of policies
- integrity checks
18. Refer to the exhibit. Which data format is used to stand for the data for network automation applications?

- XML
- YAML
- HTML
- JSON
19. What is the function of the cardinal contained in most RESTful APIs?
- Information technology is the tiptop-level object of the API query.
- It is used to cosign the requesting source.
- Information technology represents the main query components in the API request.
- It is used in the encryption of the message by an API request.
20. Which ii configuration management tools are adult using Ruby? (Cull two.)
- Boob
- Ansible
- SaltStack
- Chef
- RESTCONF
21. Which term is used to draw a gear up of instructions for execution past the configuration management tool Puppet?
- Playbook
- Cookbook
- Manifest
- Colonnade
22. Which term is used to depict a gear up of instructions for execution by the configuration management tool SaltStack?
- Cookbook
- Manifest
- Pillar
- Playbook
23. Which scenario describes the use of a public API?
- It requires a license.
- It can be used with no restrictions.
- It is used between a visitor and its business partners.
- It is used just within an system.
24. What is YAML?
- It is a scripting linguistic communication.
- Information technology is a information format and superset of JSON.
- Information technology is a compiled programming language.
- It is a web application.
25. Which RESTFul operation corresponds to the HTTP GET method?
- patch
- update
- read
26. Which technology virtualizes the network command aeroplane and moves it to a centralized controller?
- SDN
- fog computing
- cloud computing
- IaaS
27. What are two functions of hypervisors? (Choose two.)
- to sectionalisation the difficult bulldoze to run virtual machines
- to manage virtual machines
- to protect the host from malware infection from the virtual machines
- to share the antivirus software across the virtual machines
- to allocate physical organization resources to virtual machines
28. What is a difference betwixt the functions of Cloud calculating and virtualization?
- Cloud computing requires hypervisor technology whereas virtualization is a error tolerance technology.
- Cloud computing separates the awarding from the hardware whereas virtualization separates the OS from the underlying hardware.
- Cloud computing provides services on web-based access whereas virtualization provides services on data access through virtualized Internet connections.
- Deject computing utilizes data eye applied science whereas virtualization is not used in data centers.
29. How is the YAML data format structure different from JSON?
- Information technology uses indentations.
- Information technology uses terminate tags.
- It uses hierarchical levels of nesting.
- It uses brackets and commas.
30. What is the most widely used API for spider web services?
- XML-RPC
- SOAP
- JSON-RPC
- Residual
31. What is Balance?
- It is a manner to store and interchange data in a structured format.
- It is an architecture fashion for designing web service applications.
- It is a human readable data structure that is used by applications for storing, transforming, and reading data.
- Information technology is a protocol that allows administrators to manage nodes on an IP network.
32. What is a departure between the XML and HTML data formats?
- XML does not use predefined tags whereas HTML does utilise predefined tags.
- XML encloses data within a pair of tags whereas HTML uses a pair of quotation makes to enclose data.
- XML formats data in binary whereas HTML formats data in manifestly text.
- XML does non require indentation for each key/value pair only HTML does require indentation.
33. To avoid purchasing new hardware, a visitor wants to accept advantage of idle system resources and consolidate the number of servers while allowing for multiple operating systems on a single hardware platform. What service or technology would support this requirement?
- dedicated servers
- Cisco ACI
- virtualization
- software defined networking
34. Lucifer the term to the RESTful API request http://world wide web.mapquestapi.com/directions/v2/route?outFormat=json&fundamental=Key&from=San+Jose,Ca&to=Monterey,Ca component. (Not all options are used.)
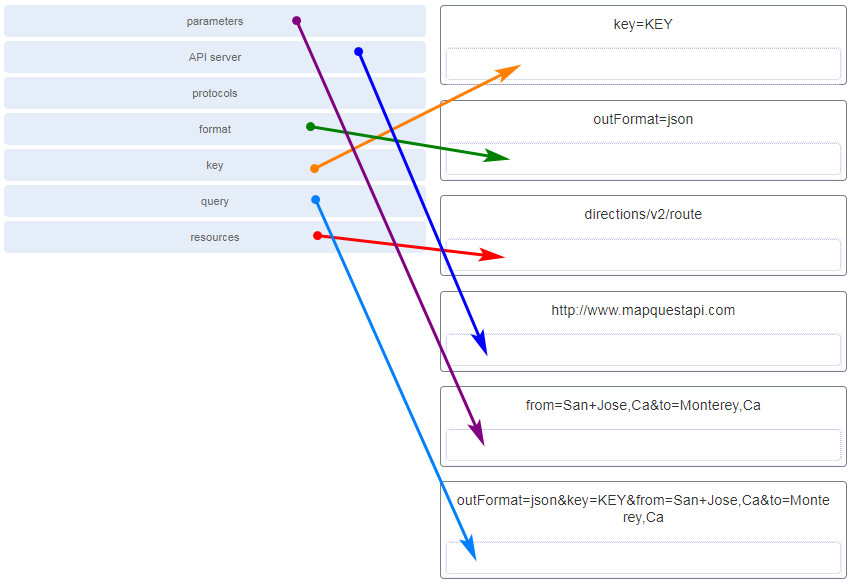
35. Which deject calculating opportunity would provide the use of network hardware such as routers and switches for a detail company?
- software as a service (SaaS)
- wireless every bit a service (WaaS)
- infrastructure equally a service (IaaS)
- browser equally a service (BaaS)
36. What component is considered the brains of the ACI architecture and translates application policies?
- the Application Network Contour endpoints
- the Nexus 9000 switch
- the hypervisor
- the Application Policy Infrastructure Controller
37. Which argument describes the concept of cloud calculating?
- separation of management aeroplane from control plane
- separation of control plane from data plane
- separation of awarding from hardware
- separation of operating system from hardware
38. In which situation would a partner API be advisable?
- an cyberspace search engine allowing developers to integrate the search engine into their ain software applications
- visitor sales staff accessing internal sales data from their mobile devices
- someone creating an account on an external app or website past using his or her social media credentials
- a vacation service site interacting with hotel databases to display information from all the hotels on its web site
39. Because of enormous growth in web traffic, a company has planned to purchase additional servers to assist handle the spider web traffic. What service or technology would support this requirement?
- virtualization
- data heart
- deject services
- dedicated servers
40. ABCTech is investigating the utilize of automation for some of its products. In club to control and test these products, the programmers require Windows, Linux, and MAC OS on their computers. What service or engineering would support this requirement?
- dedicated servers
- software defined networking
- virtualization
- Cisco ACI
41. What are iii components used in the query portion of a typical RESTful API request? (Choose three.)
- API server
- format
- parameters
- key
- protocol
- resource
42. A visitor has recently become multinational. Employees are working remotely, in different time zones, and they need access to visitor services from any place at any fourth dimension. What service or technology would back up this requirement?
- dedicated servers
- cloud services
- Cisco ACI
- virtualization
43. Following a multicontinent advertizing campaign for a new product, a company finds its customer database and volume of orders are overloading its on-site figurer systems but the company does not take any room to expand. What service or technology would support this requirement?
- cloud services
- dedicated servers
- data center
- virtualization
44. A network administrator has been tasked with creating a disaster recovery plan. As part of this program, the ambassador is looking for a backup site for all of the data on the company servers. What service or engineering science would back up this requirement?
- virtualization
- software defined networking
- data center
- dedicated servers
45. Which is a requirement of a site-to-site VPN?
- It requires hosts to use VPN client software to encapsulate traffic.
- It requires a VPN gateway at each cease of the tunnel to encrypt and decrypt traffic.
- It requires the placement of a VPN server at the edge of the company network.
- Information technology requires a client/server compages.
46. Which statement describes an of import feature of a site-to-site VPN?
- It must be statically set up.
- Afterward the initial connexion is established, it tin dynamically change connection information.
- It requires using a VPN client on the host PC.
- It is commonly implemented over dialup and cable modem networks.
- It is ideally suited for use by mobile workers.
47. Which protocol is attacked when a cybercriminal provides an invalid gateway in order to create a human being-in-the-heart attack?
- DHCP
- ICMP
- DNS
- HTTP or HTTPS
48. In which TCP attack is the cybercriminal attempting to overwhelm a target host with one-half-open TCP connections?
- reset attack
- session hijacking set on
- SYN flood set on
- port browse attack
49. Which statement describes a VPN?
- VPNs employ logical connections to create public networks through the Internet.
- VPNs employ open source virtualization software to create the tunnel through the Net.
- VPNs use defended concrete connections to transfer data between remote users.
- VPNs employ virtual connections to create a private network through a public network.
Which Statement Best Describes This Public Service Campaign?,
Source: https://itexamanswers.net/ccna-3-v7-modules-13-14-emerging-network-technologies-exam-answers.html
Posted by: parentsectirepas.blogspot.com


0 Response to "Which Statement Best Describes This Public Service Campaign?"
Post a Comment